Number System
We have already know that inside a computer system, data is stored in a format that cannot be easily read by human beings.
Number system are basically of to types:
- Non-positional number system
- Positional number system
Non-positional number system
In early days, human beings counted on fingers or with the help of stones,pebbles, or sticks.This method of counting known as non-positional number system. In this system we have symbols such as I to 1,II for 2 etc.
Positional number system
The number system that we use in our day to day life is called decimal number system or positional number system.in this system the base is 10 because there are ten digits or symbols(0,1,2,3,4,5,6,7,8,9).
Binary number system
The binary number system is exactly like the decimal number system . In this system the base is 2 instead of 10.We have only two digits 0 and 1 because of its base.
Octal number system
In octal number system the base is 8. So in this system there are 8 digits (0,1,2,3,4,5,6,7) in this system the largest single digit is 7.
Hexadecimal number system
The hexadecimal number system is one with a base of 16. The base 16 gives a choice of 16 single digits or symbols.The first 10 digits are the digits of decimal number system 0,1,2,3,4,5,6,7,8,9. The remaining six digits are denoted by A,B,C,D,E,F representing the decimal values 10,11,12,13,14,15 respectively.
Computer memory is measured in terms of how many bits it can store. Here is a chart for memory capacity conversion.
- 1 byte (B) = 8 bits
- 1 Kilobytes (KB) = 1024 bytes
- 1 Megabyte (MB) = 1024 KB
- 1 Gigabyte (GB) = 1024 MB
- 1 Terabyte (TB) = 1024 GB
- 1 Exabyte (EB) = 1024 PB
- 1 Zettabyte = 1024 EB
- 1 Yottabyte (YB) = 1024 ZB
Number System Relationship
The following table depicts the relationship between decimal, binary, octal and hexadecimal number systems.
| HEXADECIMAL | DECIMAL | OCTAL | BINARY |
|---|---|---|---|
| 0 | 0 | 0 | 0000 |
| 1 | 1 | 1 | 0001 |
| 2 | 2 | 2 | 0010 |
| 3 | 3 | 3 | 0011 |
| 4 | 4 | 4 | 0100 |
| 5 | 5 | 5 | 0101 |
| 6 | 6 | 6 | 0110 |
| 7 | 7 | 7 | 0111 |
| 8 | 8 | 10 | 1000 |
| 9 | 9 | 11 | 1001 |
| A | 10 | 12 | 1010 |
| B | 11 | 13 | 1011 |
| C | 12 | 14 | 1100 |
| D | 13 | 15 | 1101 |
| E | 14 | 16 | 1110 |
| F | 15 | 17 | 1111 |
Decimal to Binary
Decimal numbers can be converted to binary by repeated division of the number by 2 while recording the remainder. Let’s take an example to see how this happens.
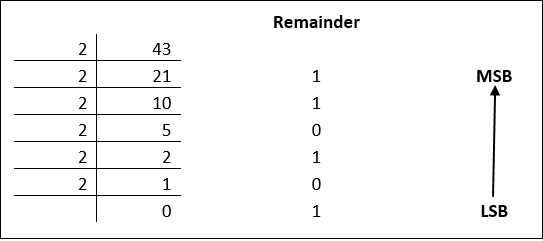
The remainders are to be read from bottom to top to obtain the binary equivalent.
4310 = 1010112
Decimal to Octal
Decimal numbers can be converted to octal by repeated division of the number by 8 while recording the remainder. Let’s take an example to see how this happens.
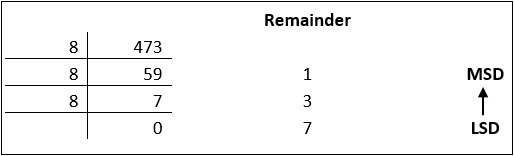
Reading the remainders from bottom to top,
47310 = 7318
Decimal to Hexadecimal
Decimal numbers can be converted to octal by repeated division of the number by 16 while recording the remainder. Let’s take an example to see how this happens.
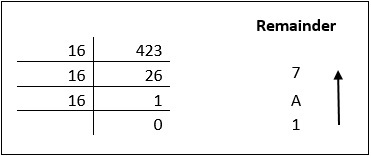
Reading the remainders from bottom to top we get,
42310 = 1A716
Binary to Octal and Vice Versa
To convert a binary number to octal number, these steps are followed −
- Starting from the least significant bit, make groups of three bits.
- If there are one or two bits less in making the groups, 0s can be added after the most significant bit
- Convert each group into its equivalent octal number
Let’s take an example to understand this.
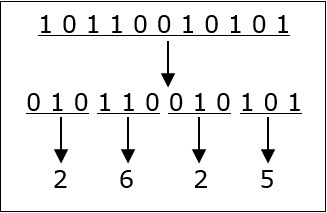
101100101012 = 26258
To convert an octal number to binary, each octal digit is converted to its 3-bit binary equivalent according to this table.
| Octal Digit | 0 | 1 | 2 | 3 | 4 | 5 | 6 | 7 |
| Binary Equivalent | 000 | 001 | 010 | 011 | 100 | 101 | 110 | 111 |
546738 = 1011001101110112
Binary to Hexadecimal
To convert a binary number to hexadecimal number, these steps are followed −
- Starting from the least significant bit, make groups of four bits.
- If there are one or two bits less in making the groups, 0s can be added after the most significant bit.
- Convert each group into its equivalent octal number.
Let’s take an example to understand this.
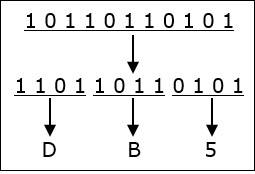
101101101012 = DB516
To convert an octal number to binary, each octal digit is converted to its 3-bit binary equivalent.
Binary to Decimal
The decimal number is equal to the sum of binary digits (dn) times their power of 2 (2n):
decimal = d0×20 + d1×21 + d2×22 + …
Example #1
Find the decimal value of 1110012:
| binary number: | 1 | 1 | 1 | 0 | 0 | 1 |
|---|---|---|---|---|---|---|
| power of 2: | 25 | 24 | 23 | 22 | 21 | 20 |
1110012 = 1⋅25+1⋅24+1⋅23+0⋅22+0⋅21+1⋅20 = 5710
Octal to Decimal
Octal to Decimal conversion is just like the Binary to Decimal
Therefore, (140)8 = (96)10.

Another Example:
(246.28)8 = (166.375)10.

Hexa to Decimal
hexa to decimal is similar to other conversions the base is 16 use at the place of 8 or 2 in hexa decimal numbers.
- Example 1: Convert (5BC)16 into the decimal system.
- Solution:To find: (5BC)16 in the decimal systemIn Hexadecimal system,5 = 5 B = 11 C = 12 Using hexadecimal to decimal formula,(5BC)16
- = ( 5 × 162 + 11 × 161 + 12 × 160 )
- 5 × 256 + 11 × 16 + 12× 1
- (1468)10
- Therefore, (5BC)16 =(1468)10
Arithmetic Operations of Binary Numbers
Binary is a base-2 number system that uses two states 0 and 1 to represent a number.
Binary additions and subtractions are performed as same in decimal additions and subtractions. When we perform binary additions, there will be two outputs: Sum (S) and Carry (C).
1. There are four rules for binary addition:
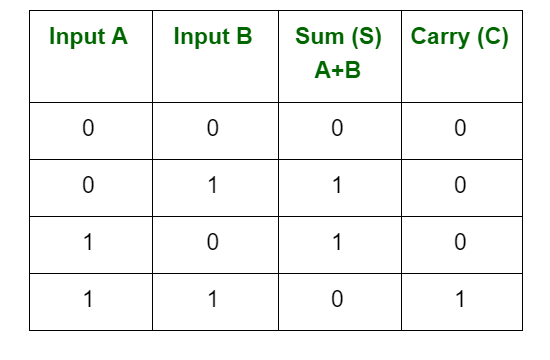
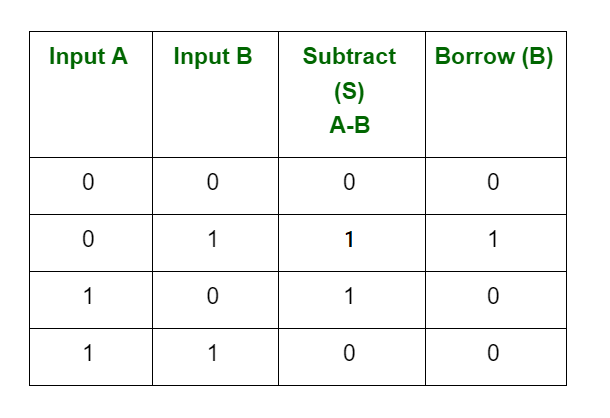
2. There are four rules for binary subtraction:
3. There are four rules for binary multiplication:
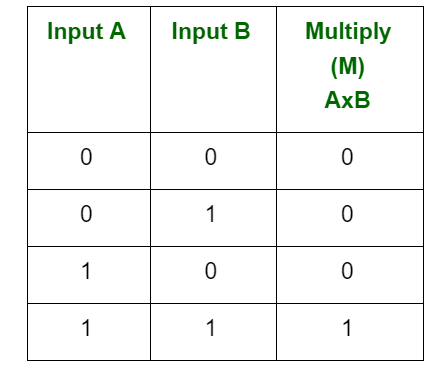
Multiplication is always 0, whenever at least one input is 0.
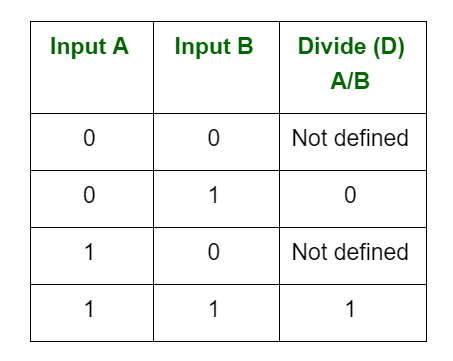
4. There are four parts in any division: Dividend, Divisor, quotient, and remainder.
What Is Computer Virus ?
A program virus is nothing but a small program written by someone to corrupt or damage the information stored in the computer system , and to replicate itself from one computer to another.
These viruses spread when someone copies a virus infected programs from one computer and runs it on some other computer.
A virus cannot spread by using any data file such as text file , image file , sound file , etc.
A virus needs some kind of executable program such as, .EXE , .COM , .SYS ,Windows, etc.
A virus can even delete everything on the hard disk.
Computer viruses can be attached by funny images , Greeting Card , Audios & Videos
A virus can be divided into different types:
- WORM
- TORJAN
- BOMB
- MBR (PARTITION TABLE) INFECTOR
- DBR (BOOT DECTOR) INFECTOR
- PROGRAM / FILE INFECTOR (PARASITIC VIRUS)
- MULTIPARTILE VIRUSES
- STEALTH VIRUSES
- POLYMORPHIC VIRUSES
- MACRO VIRUS
- WEB APPLET VIRUS
Explanation:-
WORM
Worms were one of the first computer viruses . A program written as worm virus normally do not do any destructive work, a worm’s main work is to replicate itself . The original worm programs were made as experimental programs in computer labs to test if a program can be made to replicate itself. Most of the current viruses contain a worm program in them to manage the replication part of the virus.
TROJAN
Trojan is a name given to those programs that appear as some useful utility, but they contain hidden destructive parts . A virus that has infected a useful .Com or .EXE programs makes that executable program a Trojan , the virus will become active and starts doing its job. A pure Trojan virus does not replicate itself , but currently most of the virus contain a Trojan , as well as worm , so a useful looking program can destroy the data as well as replicate itself.
BOMB
Another type of virus program is known as bombs. These are the programs that waits for some specific event event to occur and when that particular event occurs the bomb become active destroying or corrupting the information inside the computer. A virus may contain bomb ,whom and the Trojan horse all the three parts, to effectively replicate and destroy data.
MBR (PARTITION TABLE) INFECTOR
A virus can also be classified based on the area infected by a virus . A MBR or Partition table infector viruses infects the Master Boot Recorder(MBR) of the hard disk drive . These viruses become active every time the machine is booted from the hard disk drive , because during booting , first thing the BIOS does it to execute the program located in the MBR. Removing a MBR virus is very , easy as one needs to just overwrite the infected MBR code with a good MBR code
DBR (BOOT SECTOR) INFECTOR
Another virus type based on the area infected by them is DBR or DOS Boot Record infector viruses . These viruses very commonly spread through infected floppy disks. These viruses also infect the hard disk drive’s DOS partition’s boot sector and every time the machine is switched on and booted from the hard disk drive the virus becomes active in the memory.
PROGRAM/FILE INFECTOR (PARASITIC VIRUS)
Another type of virus do not infect the MBR or the DBR , instead they attach themselves to some executable program such as .EXE, .COM, .SYS, .OVL, .BIN, etc . These viruses turn the useful program which they infect into Trojan programs , anytime these infected programs are executed , the virus becomes active in memory and starts its work of replication and destruction.
MULTIPARTILE VIRUSES
A virus can contain all the above three infectors , MBR, DBR and the program infector parts in its program . This type of virus program is called multipatile virus.
STEALTH VIRUSES
Stealth viruses are special type of viruses , once they become active in memory they conceal themselves from detection . These viruses hide themselves from detection by a virus scanner, by constantly changing their code. This method used by these viruses is they copy the original part of the infected portion of the disk or program , into some other part and when the virus is active in memory , every time a scanning program checks, the uninfected part is shown to the scanner program.
POLYMORPHIC VIRUSES
Viruses that change their appearance by using the encryption method to avoid detection are known as polymorphic viruses. These viruses change their codes with each run by using some encryption viruses code and also they change their encryption method with each run making it very difficult to detect this type of viruses by using the simple virus scanning method. Continually change its appearance , This makes detection of virus using scanning method a very difficult job.
MACRO VIRUS
Macro viruses appeared after the introduction of macros in the various applications such as spreadsheet , word processor etc. Most of the macro viruses are written to infect Microsoft Word and MS EXEL. To protect from macro virus one should never open a document with attachment , without scanning it first with latest virus scanner.
WEB APPLET VIRUS
A new type of virus can be made in the web scripting language such as Active X, JavaScript , Java,etc. When a web page containing infected Active X, Javascript or Java code is opened , the virus will infect your system. Once the virus becomes active it can do all the works done by a virus such as destroying data , spreading itself etc.
Where do viruses live ?
A virus can never spread if you copy the data file from one infected floppy or hard disk drive and use it on some other clean system .on this type of situation only chance of infection comes if the date file contain some macro and is infected with a macro virus.
Keeping virus away?
To prevent a virus infection one can take some precautions such as
- Don’t use pirated software
- Get shareware for some reputed company /BBS
- Run virus scanner /checker program regularly
- Use a memory resident anti virus program
- Always keep current version of anti virus software
- Backup the date regularly
- Watch out when you get a service engineer’s visit
- Don’t open e-mail attachments from unknown address
- Take care when downloading files from internet
VIRUS INFECTION SYMPTOMS?
Some of the very common symptoms shown by a system infected by a virus are given next.
- Unexplained slowdown of the system
- Decrease in the amount of available memory
- Increases in bad sector /lost cluster etc.
- Can’t execute executable file
- Screen shows some unusual outputs
- Drive’s light turns on
- New”.com” files appear for the “.exe” files
ANTI-VIRUS SOFTWARE
There are basically four type of antivirus software, they are
- Checksum (crc) type
- TSR (activity monitor) type
- Scanner type
- Program screeners
WHAT TO DO AFTER INFECTION ?
Once the system becomes infected with virus, your first aim should be to recover as much as important data as possible. Next ,you should try to remove the infection from the system
If the virus cannot be removed them you can delete the infected file, format the drive unconditionally ,so that no undelete information is saved or you can low-level format the drive to remove any trace of the virus.
If the virus has infected MBR,DBR or some executable programs then you can recover from this
AFTER RECOVERY
Once the virus is removed from the system, you need to do some data recovery. The virus might have destroyed some data ,deleted some files , or corrupted the FAT(File Allocation Table) etc. Run the SCANDISK or CHKDSK program to find out if any lost clusters or some other logical error exists on the drive. Convert any lost cluster into file and check these files for any useful data.
SOME COMMON VIRUS MYTHS
- Virus can destroy all data on disk
- If a file is damaged it must be some virus infection
- Virus can hide in data file
- Data Backup after virus infection is useless
- Read/Only files are safe from virus
- Write protected floppies can be infected by virus
- Anti-virus software or hardware can protect from all viruses
Anti-virus
Anti-virus is a security program you install on your computer or mobile device to protect it from getting infected by malware.